My Kubernetes exploration brought me to the topic of privileged pods. Privileged pod, or container running in privileged mode is a configuration option of K8s deployment which can be useful, but can also be dangerous.
This is an excerpt of deployment specification where privileged mode defined.
kind: Deployment
...
spec:
template:
spec:
containers:
- name: ...
image: nginx:1.14.2
securityContext:
privileged: true
Found this article:
https://www.cncf.io/blog/2020/10/16/hack-my-mis-configured-kubernetes-privileged-pods/
which explains about what's the true intent of running privileged pod and the security risk it caused, including how to exploit privileged pod to do malicious intent.
Now the question is, how can we prevent container with privileged mode to run on our Kubernetes cluster?
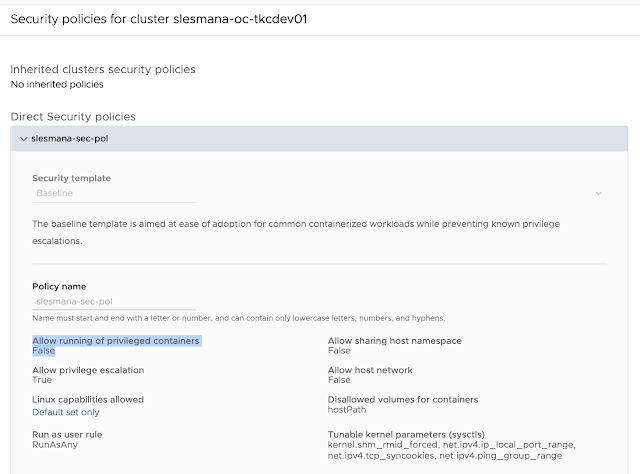
In Tanzu Misison Control (TMC), we can quickly do that by assigning Security Policy to the target Kubernetes cluster. Here in the sample I create a Security Policy using baseline security template and apply it to my cluster slesmana-oc-tkcdev01. Baseline security template include configuration to NOT allow running of privileged containers as seen below in the screenshot.
Checking to the events, it shows admission webhook denied the request to enforce security policy defined in tmc.cp.slesmana-sec-pol, which is the Security Policy I created above, and the reason is because the pod have security context specification of privileged set to True.
Error creating: admission webhook "validation.gatekeeper.sh" denied the request: [tmc.cp.slesmana-sec-pol] Privileged container is not allowed: nginx, securityContext: {"privileged": true}


No comments:
Post a Comment